The Strategist's Guide to Tenable: Mastering Exposure Management in the Modern Threat Landscape
How the Pioneer of Risk-Based Vulnerability Management is Transforming Enterprise Security
In Part 1 of this series, we explored the evolution from vulnerability management to exposure management. In Part 2, we examined Rapid7's strategy. Now, in Part 3, we turn to Tenable—a pioneer in vulnerability management—to analyze its product ecosystem, vision, and how it's reshaping the cybersecurity landscape.
From Nessus to Exposure Management: Tenable's Remarkable Journey
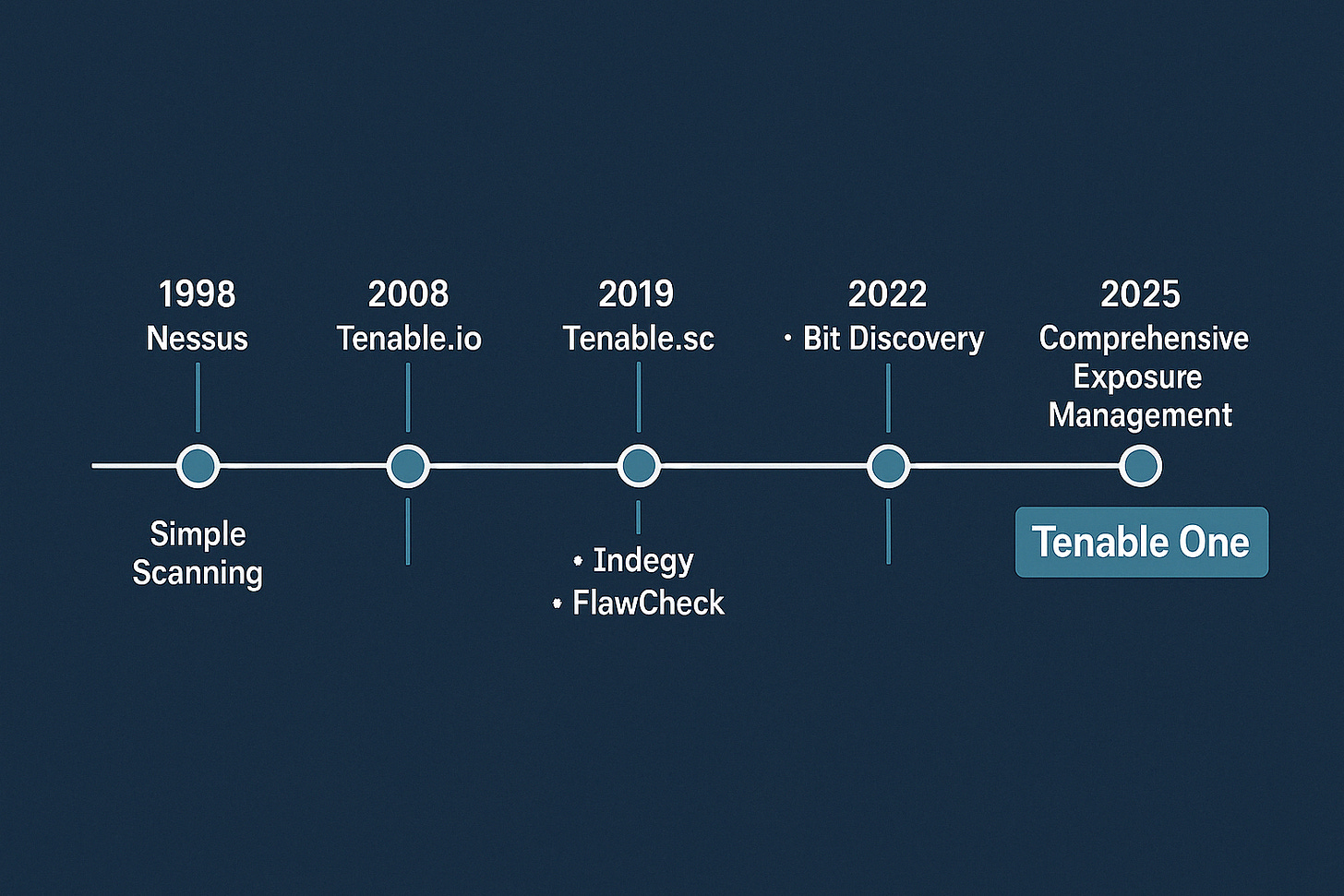
Remember the late 1990s when Nessus emerged as an open-source vulnerability scanner? Fast forward to today, and that same technology has evolved into the cornerstone of a cybersecurity giant that's pioneering the concept of "exposure management." Tenable's transformation from a vulnerability scanning company to the self-proclaimed "Exposure Management company" represents one of the most fascinating strategic pivots in cybersecurity.
But why should security leaders care? Because Tenable's evolution mirrors the industry's own journey from reactive vulnerability whack-a-mole to proactive, business-aligned risk management.
The Tenable Arsenal: A Cybersecurity Swiss Army Knife
Tenable's product ecosystem has grown from a single vulnerability scanner into a comprehensive platform of integrated solutions:
Nessus: The industry-standard vulnerability scanner with over 100,000 plugins covering everything from traditional IT to cloud infrastructure
Tenable Vulnerability Management (formerly Tenable.io): Cloud-based enterprise vulnerability management platform delivering unified visibility
Tenable Security Center (Tenable.sc): On-premises vulnerability management for organizations with strict data sovereignty requirements
Tenable One: The company's flagship exposure management platform integrating six core products across vulnerability scanning, web applications, cloud security, Active Directory protection, and external attack surface management
What makes this arsenal particularly compelling is its breadth of coverage. While competitors often specialize in specific domains, Tenable offers comprehensive visibility across IT, cloud, containers, operational technology (OT), Active Directory, and external assets—all through a single pane of glass.
For CISOs navigating today's complex threat landscape, this flexibility is invaluable. Whether you're a cloud-first organization or managing critical infrastructure with air-gapped networks, Tenable offers deployment options to match your security posture and compliance requirements.
Beyond Box-Checking: Tenable's Vision for the Future
"Finding vulnerabilities isn't the hard part anymore—it's knowing which ones actually matter."
This sentiment captures the essence of Tenable's strategic vision. While traditional vulnerability management drowns security teams in endless lists of CVEs, Tenable has pioneered a risk-based approach focused on identifying the critical 3% of vulnerabilities that truly threaten your business.
Through strategic acquisitions, Tenable has systematically expanded its capability to assess risk across multiple domains:
OT Security: With Indegy acquisition (2019)
Active Directory Security: Through Alsid (2021)
Cloud Security: Via Accurics/Ermetic (2022)
External Attack Surface Management: From BitDiscovery (2022)
Attack Path Analysis: With Cymptom (2022)
Remediation Orchestration: Most recently with Vulcan Cyber (2025)
These moves reveal a deliberate strategy: provide a holistic risk platform covering identification and prioritization of vulnerabilities across all asset types. As Forrester's analyst Erik Nost observed, "Tenable has created a holistic offering by taking advantage of strategic M&A to move into OT and cloud security," accelerating its shift from pure vulnerability management to exposure management.
Perhaps most impressively, Tenable's Vulnerability Priority Rating (VPR) has revolutionized how organizations prioritize remediation. By incorporating threat intelligence and real-world exploitation data, VPR helps security teams focus on vulnerabilities that are actively being exploited—not just those with high CVSS scores. This context-driven approach is transforming how organizations allocate their limited security resources.
The Competitive Edge: Where Tenable Shines
In the fiercely competitive vulnerability management market, Tenable distinguishes itself in several key areas:
Unmatched Scanning Depth: With over 100,000 plugins, Tenable's scanning technology provides industry-leading vulnerability coverage and accuracy. Few competitors can match this level of technical depth.
Superior Risk Analytics: Tenable was early to incorporate threat intelligence into vulnerability management. Their Predictive Prioritization/VPR model and Lumin risk scoring help teams focus on vulnerabilities that actually matter.
Single Platform, Multiple Domains: Tenable One provides a unified view of vulnerability, cloud, identity, and external attack surface risks—something few competitors can match. This comprehensive visibility is crucial for understanding true enterprise risk.
Hybrid Deployment Flexibility: Unlike most competitors, Tenable offers both cloud and on-premises solutions. Organizations that can't use SaaS for scanning can deploy Tenable.sc internally while still leveraging Tenable One for analytics.
Trusted by Practitioners: Thanks to Nessus's legacy, Tenable enjoys strong credibility among technical users. This community trust isn't just about brand—it translates to faster adoption and smoother implementation.
In Forrester's 2023 Vulnerability Risk Management Wave, Tenable maintained its leadership position while both Rapid7 and Qualys fell from the leaderboard—a testament to Tenable's forward-thinking approach to evolving vulnerability management into exposure management.
The Challenges: Room for Improvement
Despite its strengths, Tenable isn't without challenges:
Integration Growing Pains: Tenable's rapid expansion through acquisitions has sometimes led to a fragmented user experience. While Tenable One aims to unify these different tools, customers may still encounter some product silos as integration matures.
Risk Scoring Transparency: Tenable's risk scoring has been criticized as something of a "black box." Organizations may struggle to understand exactly why a particular vulnerability has a specific VPR score, though Tenable is working to improve score explainability.
Third-Party Data Integration: Although Tenable excels at analyzing data from its own scanners, it has historically been less adept at ingesting vulnerability data from third-party tools—an area where specialized risk platforms like Vulcan Cyber (which Tenable just acquired) have excelled.
Remediation Workflow: While Tenable excels at identifying and prioritizing vulnerabilities, its capabilities for managing the actual remediation process have been less mature. The recent Vulcan Cyber acquisition should significantly strengthen this aspect.
Competition in Specialized Domains: Particularly in cloud security, Tenable faces competition from dedicated Cloud-Native Application Protection Platforms (CNAPPs) like Wiz and Orca Security, which may offer deeper cloud-specific capabilities.
Tenable vs. The Competition: Strategically Different Approaches
The "big three" in vulnerability management—Tenable, Rapid7, and Qualys—have each evolved distinct strategic approaches:
Tenable positions itself as the exposure management leader, focusing on providing a comprehensive view of cyber risk across multiple domains.
Rapid7 aims to be the unified security operations platform, integrating vulnerability management with SIEM, EDR, and other security tools for a seamless practitioner experience.
Qualys continues as the reliability and breadth player in vulnerability and compliance management, often favored by auditors and organizations with comprehensive compliance requirements.
If you're a CISO looking to build a modern vulnerability management program, your choice among these vendors likely depends on your specific priorities. If your focus is on integrated security operations, Rapid7's unified platform might appeal. If compliance reporting is your primary concern, Qualys's comprehensive modules could be attractive.
But if your goal is to transform vulnerability management into a strategic risk reduction program—with broad visibility, threat context, and analytics to drive decision-making—Tenable's exposure management approach offers compelling advantages.
Looking Ahead: The Future of Exposure Management
As cyber threats continue to evolve, the vulnerability management space is undergoing a profound transformation. Tenable's journey from Nessus to Tenable One represents the vanguard of this shift—from reactive vulnerability scanning to proactive exposure management.
With its recent leadership changes (appointing long-time executives as co-CEOs in April 2025) and the strategic acquisition of Vulcan Cyber, Tenable is doubling down on its vision of creating "the most comprehensive exposure management platform on the market."
For security leaders, the key question isn't just which tool to select—it's how to leverage these evolving capabilities to stay ahead of attackers. Tenable's platform provides the visibility and analytics to identify your most critical exposures, but organizations must still develop the processes to quickly act on this intelligence.
As the attack surface continues to expand and adversaries grow more sophisticated, the ability to cut through the noise and focus on what truly matters becomes ever more crucial. By pioneering the shift from vulnerability counting to exposure-focused cyber risk management, Tenable is helping security teams transform from reactive firefighting to strategic business enablement.
The tools are improving rapidly—now it's up to organizations to use them wisely in the ongoing battle to reduce cyber risk.